As businesses continue to embrace cloud technology, securing cloud environments has become more critical than ever. While the cloud offers incredible benefits such as scalability, flexibility, and cost efficiency, it also brings new challenges in terms of data protection and system vulnerabilities. In fact, 94% of enterprises use cloud services, but many still struggle to maintain strong security practices.
In this blog, we’ll explore the best practices for securing cloud environments, providing you with actionable steps to protect sensitive data, prevent breaches, and ensure that your cloud infrastructure remains safe and compliant. By adopting these strategies, you can confidently navigate the complexities of cloud security and minimize the risks associated with cloud adoption.
The average cost of a data breach in 2024 is $4.88 million, which includes direct losses, reputation loss, and compliance fines. – MasterOfCode
Importance of Cloud Security
The rapid adoption of cloud technology has revolutionized the way businesses operate, but it has also made cloud environments an attractive target for cybercriminals. Without proper security measures, organizations face risks such as data breaches, ransomware attacks, unauthorized access, and compliance violations.
Here are some key reasons why cloud security should be a top priority:
1. Protection Against Evolving Threats
Cloud environments are constantly exposed to sophisticated threats, including phishing, malware, and zero-day vulnerabilities. A proactive security strategy helps mitigate these risks and keeps your data and systems safe.
2. Safeguarding Sensitive Data
Many organizations store confidential customer information, financial records, and intellectual property in the cloud. A single breach can lead to severe financial losses, reputational damage, and legal consequences.
3. Ensuring Compliance
Industries such as healthcare, finance, and e-commerce are governed by strict regulations like GDPR, HIPAA, and PCI DSS. Maintaining cloud security ensures compliance and avoids hefty penalties for non-compliance.
4. Business Continuity
Cyberattacks can disrupt operations, leading to downtime and loss of revenue. A robust cloud security framework ensures operational resilience and minimizes downtime in the event of an attack.
45% of data violations are cloud-based, and 82% of those involve cloud-stored data. – Korcomptenz
Actionable Tips for Securing Cloud Environments
Implementing strong security measures is essential to protect your cloud environment from potential threats. Below are actionable tips to help secure your cloud infrastructure effectively:
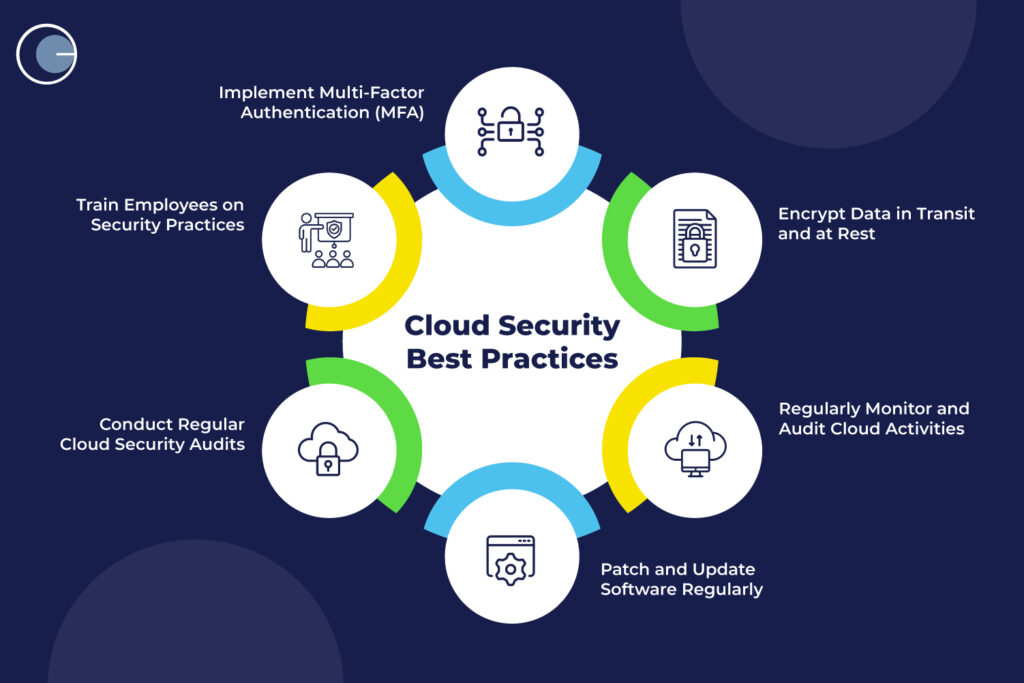
1. Implement Strong Identity and Access Management (IAM)
- Enforce Multi-Factor Authentication (MFA): Require multiple authentication steps to verify user identities.
- Apply the Principle of Least Privilege (PoLP): Grant users and systems the minimum permissions needed to perform their tasks.
- Regularly Review Access Controls: Audit and update user permissions to prevent unauthorized access.
2. Encrypt Data in Transit and at Rest
- Use Encryption Protocols: Protect data in transit with protocols like TLS and secure data at rest with AES encryption.
- Secure Backups: Ensure backups are encrypted and stored in isolated environments to prevent unauthorized access.
3. Monitor and Log All Activities
- Centralize Logging: Use tools like SIEM (Security Information and Event Management) systems to consolidate and analyze logs.
- Set Up Alerts: Configure alerts for unusual activities, such as login attempts from unfamiliar locations.
- Regularly Audit Logs: Review logs to identify potential vulnerabilities or attacks.
4. Regularly Patch and Update Software
- Automate Patch Management: Use automation tools to apply updates and patches across all systems and applications.
- Monitor Vulnerabilities: Stay informed about newly discovered vulnerabilities in third-party services and dependencies.
5. Conduct Regular Cloud Security Audits
- Review Security Configurations: Evaluate firewall rules, storage permissions, and network configurations for misconfigurations.
- Test for Compliance: Ensure your cloud setup aligns with regulatory frameworks like GDPR, HIPAA, or SOC 2.
6. Train Your Team on Cloud Security Practices
- Employee Awareness: Conduct regular training sessions to educate employees about phishing and other common cyber threats.
- Specialized Training for IT Teams: Equip IT and DevOps teams with the skills to address cloud-specific security challenges.
Some of the top cloud security trends for 2024 include a rise in zero-trust security models, increased use of AI and ML for threat detection, and automation of security in DevOps. – SentinelOne
Industry Best Practices and Standards
Adopting industry-recognized standards and best practices is crucial for maintaining a secure and compliant cloud environment. These frameworks provide guidelines to safeguard sensitive data, prevent breaches, and align with regulatory requirements.
1. Follow Security Frameworks
- ISO 27001: Focuses on information security management systems, offering a comprehensive approach to securing cloud environments.
- NIST Cybersecurity Framework: Provides guidelines for identifying, protecting, detecting, responding to, and recovering from cybersecurity incidents.
- CIS Controls: Offers prioritized actions and best practices to secure IT systems and data.
2. Maintain Compliance with Industry Regulations
- HIPAA (Healthcare): Ensure the protection of sensitive patient data stored in the cloud.
- GDPR (General Data Protection Regulation): Safeguard personal data and comply with data privacy laws.
- PCI DSS (Payment Card Industry Data Security Standard): Secure payment card transactions and cardholder data.
3. Leverage Cloud Provider Security Tools
Most major cloud providers offer built-in security tools and services to enhance your security posture:
- AWS: Utilize AWS Identity and Access Management (IAM), GuardDuty, and CloudTrail for logging and threat detection.
- Microsoft Azure: Leverage Azure Security Center, Azure Policy, and Key Vault to secure your resources.
- Google Cloud Platform (GCP): Use Cloud Security Command Center, Identity-Aware Proxy, and encryption tools.
4. Use Third-Party Assessments and Certifications
- Engage independent auditors to evaluate your cloud environment for vulnerabilities.
- Look for certifications such as SOC 2, which demonstrates robust security practices.
5. Automate Compliance Monitoring
Use tools that automatically assess your cloud environment for compliance with industry standards. Automation ensures continuous monitoring and helps address issues proactively.
Conclusion
Securing your cloud environment is not just a necessity—it’s a business imperative. By implementing best practices like strong access controls, encryption, regular audits, and continuous monitoring, you can safeguard sensitive data, ensure compliance, and protect your organization from evolving cyber threats.
However, navigating the complexities of cloud security can be challenging without the right expertise. That’s where Charter Global comes in.
With a proven track record in Cloud Security Audits, DevOps Services, and Cloud Infrastructure Automation, Charter Global offers tailored solutions to secure your cloud environment while ensuring optimal performance and compliance. Our team of experts works closely with you to assess vulnerabilities, implement robust security measures, and build a resilient cloud infrastructure.
Take the next step in protecting your business.
Contact Charter Global today.
Book a Consultation.
Or email us at [email protected] or call +1 770-326-9933.
